Verify Any User Data
On The Internet in 30 Seconds.
Verify Any User Data
On The Internet in
30 Seconds.
Verify Any User Data
On The Internet in
30 Seconds.
YC-backed • Trusted Globally • Series A
YC-backed • Trusted Globally • Series A
YC-backed • Trusted Globally • Series A
Status Match
Memberships &
Subscriptions
ID Verification
Education
Verification
Employment & Income
Verification








Status Match
100+ Loyalty Programs
•
Deeper Insights
•
Personalized Offers
Learn more

Status Match
Memberships &
Subscriptions
ID Verification
Education
Verification
Employment & Income
Verification








Status Match
100+ Loyalty Programs
Deeper Insights
Personalized Offers
Learn more

Connect and Verify data trapped behind logins, with user consent.
Connect and Verify data trapped behind logins, with user consent.
Connect and Verify data trapped behind logins, with user consent.
Connect and Verify data trapped behind logins, with user consent.
30M+ Hours
30M+ Hours
30M+ Hours
Verification Time Saved
Verification Time Saved
Verification Time Saved
Live Verification Counter
Live Verification Counter
Live Verification Counter
$30,000,000+
$30,000,000+
$30,000,000+
Fraud Free Savings
Fraud Free Savings
Fraud Free Savings
User-Consented Verification
User-Consented Verification
User-Consented Verification

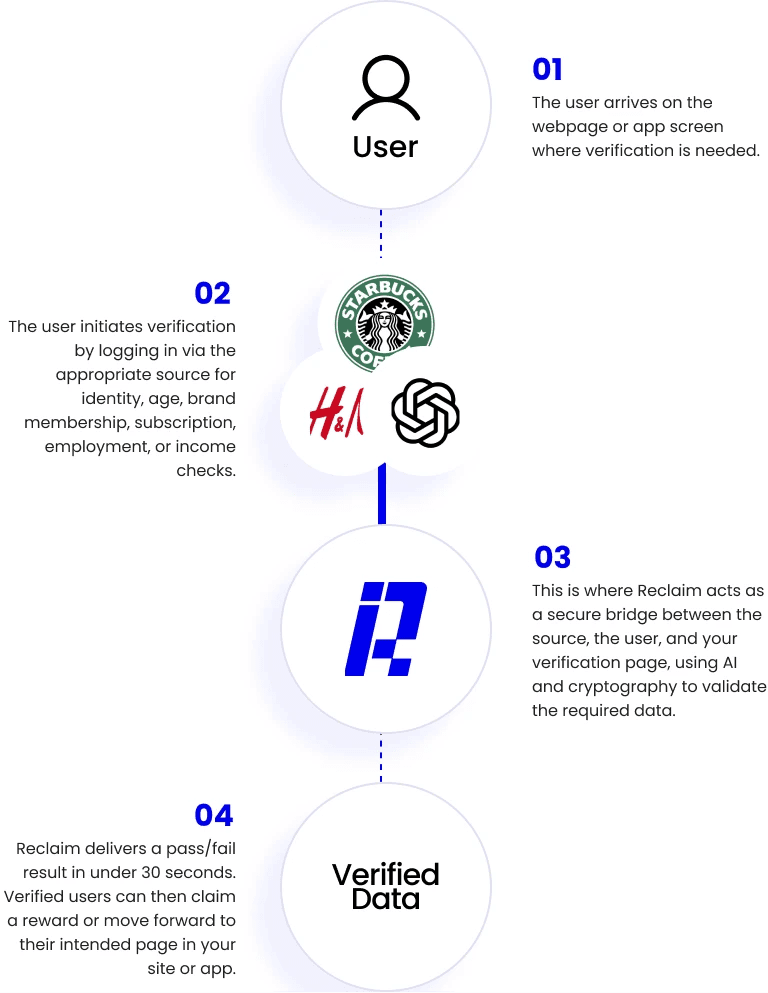


A Future-proof Verification Stack
A Future-proof Verification Stack
A future-proof verification stack
No API? No problem.
No API? No problem.
No API? No problem.
Get verified information from websites, even if they don't expose APIs
Get verified information from websites, even if they don't expose APIs
Get verified information from websites, even if they don't expose APIs
20k+ Data Sources
20k+ Data Sources
20k+ Data Sources
Choose from 20K+ prebuilt integrations, or build one yourself
Choose from 20K+ prebuilt integrations, or build one yourself
Choose from 20K+ prebuilt integrations, or build one yourself
See all supported integrations
Check Case Studies
Provably 0% Fraud
Provably 0% Fraud
Provably 0% Fraud
Reclaim Protocol uses advance cryptography to verify. Making it fraud resistant. Even AI generated fraud.
Reclaim Protocol uses advance cryptography to verify. Making it fraud resistant. Even AI generated fraud.
Reclaim Protocol uses advance cryptography to verify. Making it fraud resistant. Even AI generated fraud.
Compliant and User Consented
Compliant and User Consented
Compliant and User Consented
Make sure your data verification pipeline is secure
and compliant.
Make sure your data verification pipeline is secure
and compliant.
Make sure your data verification pipeline is secure and compliant.
Secure & Compliant
Secure & Compliant



Learn how Reclaim Protocol can solve your verifications problem
Learn how Reclaim Protocol can solve your verifications problem
Learn how Reclaim Protocol can solve your verifications problem
Learn how Reclaim Protocol can solve your verifications problem
Backed by the best
Backed by the best
Backed by the best

Secure & Compliant






Instant verification in 30secs.
No documents, no AI fraud.
User Consented & Compliant Verification
Status Match
Memberships &
Subscriptions
ID Verification
Education
Verification
Employment & Income
Verification








Status Match
100+ Loyalty Programs
•
Deeper Insights
•
Personalized Offers
Learn more

Status Match
Memberships &
Subscriptions
ID Verification
Education
Verification
Employment & Income
Verification








Status Match
100+ Loyalty Programs
•
Deeper Insights
•
Personalized Offers
Learn more

A Future-proof Verification Stack
A future-proof verification stack
No API? No problem.
Get verified information from websites, even if they don't expose APIs
Provably 0% Fraud
Reclaim Protocol uses advance cryptography to verify. Making it fraud resistant. Even AI generated fraud.
Compliant and User Consented
Make sure your data verification pipeline is secure and compliant.
20k+ Data Sources
Choose from 20K+ prebuilt integrations, or build one yourself